Top Essay Writers
Our top essay writers are handpicked for their degree qualification, talent and freelance know-how. Each one brings deep expertise in their chosen subjects and a solid track record in academic writing.
Simply fill out the order form with your paper’s instructions in a few easy steps. This quick process ensures you’ll be matched with an expert writer who
Can meet your papers' specific grading rubric needs. Find the best write my essay assistance for your assignments- Affordable, plagiarism-free, and on time!
Posted: February 4th, 2024
Mal-Adware Detection
Our project is mainly going to focus on developing a tool which would give an output and it will show whether the URL is secure or not.
Students often ask, “Can you write my essay in APA or MLA?”—and the answer’s a big yes! Our writers are experts in every style imaginable: APA, MLA, Chicago, Harvard, you name it. Just tell us what you need, and we’ll deliver a perfectly formatted paper that matches your requirements, hassle-free.
Let us try to understand this in a simpler way.
A user will enter a URL in the tool that we have developed. As soon as the URL is entered it will start extracting the HTML code. Now, when this HTML code is extracted it would have the code for the whole website. Now, the HTML code is going to be separated with the help of Document Object Model (DOM). Jsoup is a library we are going to implement to separate the HTML code form other languages.
Apart from Jsoup we have also taken the help of one more library named MessgaeDigest. Here it will filter most of the adverts, frames, images and objects. Here, the first step is achieved of extracting the code. Now the second step of generating the signature of that code would start and that is done with the help of MD5.The MD5 message-digest algorithm is easy and simple to implement and provides a fixed size message digest or “fingerprint” corresponding to a message of variable size. This code is then converted into hashes of fixed length.
Now comes the third step of comparing these hashes with a static database named VirusShare. It is a database that contains nearly 300 to 400 files. Each file consists of hashes of 300 to 400 adwares. So, after comparison it will give an output saying which are the harmful adwares present and whether the site is secure or not. If, it is secure then the user can move ahead and search on the site other it will tell the user not to move ahead.
Absolutely, it’s 100% legal! Our service provides sample essays and papers to guide your own work—think of it as a study tool. Used responsibly, it’s a legit way to improve your skills, understand tough topics, and boost your grades, all while staying within academic rules.
Now, comes the fourth and the last step. As, the technology is advancing daily there are various adwares that are getting created daily and so there would be various adwares that won’t be present in these files also of Virus Share. So, now it is the duty of the administrator to research about the adware and find out whether the adware is harmful or not and if it is harmful the he has to manually add into the static database of Virus Share. As, we are working on a static database it is the duty of the administrator to add the hashes manually every time. So, that the next time the same virus is found then administrator does not have to add once again in the database.
Table of Contents
Our pricing starts at $10 per page for undergrad work, $16 for bachelor-level, and $21 for advanced stuff. Urgency and extras like top writers or plagiarism reports tweak the cost—deadlines range from 14 days to 3 hours. Order early for the best rates, and enjoy discounts on big orders: 5% off over $500, 10% over $1,000!
Yes, totally! We lock down your info with top-notch encryption—your school, friends, no one will know. Every paper’s custom-made to blend with your style, and we check it for originality, so it’s all yours, all discreet.
No way—our papers are 100% human-crafted. Our writers are real pros with degrees, bringing creativity and expertise AI can’t match. Every piece is original, checked for plagiarism, and tailored to your needs by a skilled human, not a machine.
1.2.4 Functional and Non-functional requirements:
We’re the best because our writers are degree-holding experts—Bachelor’s to Ph.D.—who nail any topic. We obsess over quality, using tools to ensure perfection, and offer free revisions to guarantee you’re thrilled with the result, even on tight deadlines.
1.2.9 Assumptions and Constraints
2.1 Description of Implementation
Our writers are top-tier—university grads, many with Master’s degrees, who’ve passed tough tests to join us. They’re ready for any essay, working with you to hit your deadlines and grading standards with ease and professionalism.
Always! We start from scratch—no copying, no AI—just pure, human-written work with solid research and citations. You can even get a plagiarism report to confirm it’s 95%+ unique, ready for worry-free submission.
2.4.1 Prototype of the Project:
2.4.2 Encrypted Malware Database
You bet! From APA to IEEE, our writers nail every style with precision. Give us your guidelines, and we’ll craft a paper that fits your academic standards perfectly, no sweat.
Yep! Use our chat feature to tweak instructions or add details anytime—even after your writer’s started. They’ll adjust on the fly to keep your essay on point.
2.6.1 System Security Features
2.6.2 Security Set Up During Implementation
3.1. Hardware, Software, Facilities, and Materials
Easy—place your order online, and your writer dives in. Check drafts or updates as you go, then download the final paper from your account. Pay only when you’re happy—simple and affordable!
Super fast! Our writers can deliver a quality essay in 24 hours if you’re in a pinch. Pick your deadline—standard is 10 days, but we’ll hustle for rush jobs without skimping.
3.3.2 Training of Implementation Staff
Definitely! From astrophysics to literary theory, our advanced-degree writers thrive on tough topics. They’ll research deeply and deliver a clear, sharp paper that meets your level—high school to Ph.D.
MessageDigest messageDigest = MessageDigest.getInstance(“MD5”);
APPENDIX A: Project Implementation Report Approval
We tailor your paper to your rubric—structure, tone, everything. Our writers decode academic expectations, and editors polish it to perfection, ensuring it’s grade-ready.
APPENDIX D: System Hardware Inventory
APPENDIX E: System Software Inventory
Table 1 Functional and Nonfunctional Requirements
Upload your draft, tell us your goals, and our editors will refine it—boosting arguments, fixing errors, and keeping your voice. You’ll get a polished paper that’s ready to shine.
Table 3 Document Submission Details
Table 4 Implementation Schedule
Sure! Need ideas? We’ll pitch topics based on your subject and interests—catchy and doable. Pick one, and we’ll run with it, or tweak it together.
Figure 3 System Organization Steps
Figure 4 System Organization Steps 2
Figure 6 Virus Share Database Example
Yes! If you need quick edits, our team can turn it around fast—hours, not days—tightening up your paper for last-minute perfection.
Figure 8 Implementation of Jsoup Algorithm
Figure 9 Outcome of Jsoup implementation
Figure 10 EasyList Rule Used in Project
Figure 11 Implementation Code of EasyList
Figure 12 Outcome of EasyList Implementation
Figure 13 Implementation of MD5 Algorithm…1
Absolutely! We’ll draft an outline based on your topic so you can approve the plan before we write—keeps everything aligned from the start.
Figure 14 Implementation of MD5 Algorithm…2
Figure 15 Outcome of MD5 Algorithm
Malware analysis and detection is an upcoming problem of Cybersecurity due to increase in ad links on screen that propagates user to click on or sometime download malicious payload that leads to severe attacks like ransom ware most in common. Our project is based on this problem to implement malware detection tool that will extract all ad links from a source web page(web scraping) and generates their hashes(fingerprints) in order to compare with them stored hashes(repository) and test their status(whether good or bad one).
Malwares detection is of paramount importance to digital era as more than 16 million malwares have been evolved since 2016/2017.Malware detection can be done through various techniques like static or dynamic analysis, but we implemented static approach using MD5 algorithm due to time constraints. No doubt dynamic analysis is a better solution for obfuscated samples as run time behavior (polymorphic) can be better traced.
Malware codes can be embedded into source page of websites or any software applications. It can be Trojans, worms, backdoors or rootkits. On may4, 2010, a small malware code hit around 16000 host computers that generates DOS attack on server. Due to increase in number of sheer malwares, it is becoming quite important to detect their classifications and families. Attackers basically use reuse of codes of previous malwares to generate new one. Malware detection can be done in two ways: Behavior analysis (study of known patterns and behavior) and static signature based (study of signatures and comparing with repository of stored signatures and adding new signatures manually).
Malware detection helps in protection of same or other systems. It is an implementation technique for detecting malicious behaviors. Now days it is very important method used for preventing zero-day attacks (no prior clues).
Attackers using advertisements as their weapon to plan and execute cyber-attacks on end user systems as through advertisements malicious code will spread immediately and can infect thousands of thousands of computers with in a second. This is main point of consideration in our project. Extraction of ad links(malicious) from web page is quite important as these ads contains malicious content that could lead to severe attacks likeDOS, identity theft.
Project Planning comprises of 4 different phases:
You bet! Need stats or charts? Our writers can crunch numbers and craft visuals, making your paper both sharp and professional.
Analysis: It involves analysis of malwares and adwares and techniques used to detect and prevent end systems from Malvertising attacks. It involves research of what platform we needed, how to implement code, how to test tool in real time environment.
Designing: It includes designing of graphical user interface. The main part is to design components of system in order to verify correct flow within the specified system, system flow chart, system specifications.
Implementation: It involves implementing basic functionality with help of language (Java) on android platform.
Testing: It involves testing system against desired test cases.
| Tools | Description |
| Libraries: Jsoup, messagedigest | Jsoup acts as parser on html web page and message digest used to generate hash of given ad link |
| Database | A repository called as Virus Share that contains 300 to 400 hashes in one file is embedded in source programming |
| Simulation of android platform | Android studio 3.2.1 |
| Number of test cases to be generated | At least 5 for different html tags |
| MS word, PowerPoint | To report details of project, evidence and implementation |
Table 1 Functional and Nonfunctional Requirements
1.2.5 Resources imported
Project implementation is based on static analysis using signature-based approach. So, list of new malware signatures would be updated timely in order to detect new malwares (polymorphic in nature).
Four stages of tool implementation
We break it down—delivering each part on time with consistent quality. From proposals to final drafts, we’re with you all the way.
Web URL search box in android emulator.Purpose to enter Web URL is to scarp all links on android emulator
Web scraping using jsoup library. Comparing ad links with regular expressions stored in easy list EasyList acts as primary filter that detects adverts from links extracted including unwanted iframes, images and objects. This list consists of around 3000 regular expression of ad links and is used by ad blockers, ad block plus.
Message Digest5(MD5) to generate signature of code: The MD5 message-digest algorithm is easy and simple to implement and provides a fixed size message digest or “fingerprint” corresponding to a message of variable size. Message Digest 5 Invented By Ronalt Rivest In 1991 is a cryptographic Function That Is Used To Verify Integrity Of File. It acts as checksum on dataset. It basically takes random data as input and generates fixed size hash (32 hexadecimal code) as output as shown below
e4d909c290d0fb1ca068ffaddf22cbd0
Hashing is a common method to uniquely identify malwares. Hash basically signifies signatures of malwares (fingerprints). The MD5 algorithms requires following five steps to calculate the message digest or hash value of the message.
Yep! Whether it’s UK, US, or Australian rules, we adapt your paper to fit your institution’s style and expectations perfectly.
MD5 works on the basis of five steps.
Comparing hashes with stored hashes and if it matches, displaying its status after testing.
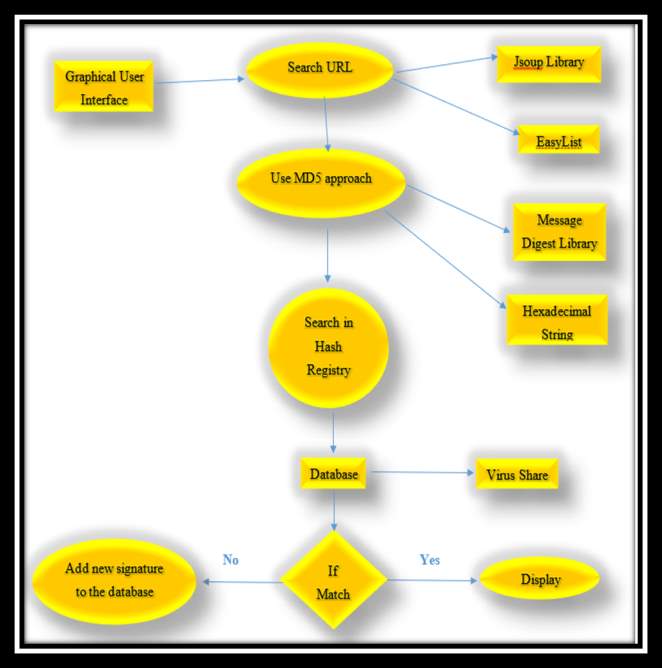
This section is an interpretation of what we using to implement basic purpose of tool (detection of mal-ad wares). It comprises of following components:
We write every paper from scratch just for you, and we get how important it is for you to feel confident about its originality. That’s why we double-check every piece with our own in-house plagiarism software before sending it your way. This tool doesn’t just catch copy-pasted bits—it even spots paraphrased sections. Unlike well-known systems like Turnitin (used by most universities), we don’t store or report anything to public databases, so your check stays private and safe. We stand by our plagiarism-free guarantee to ensure your paper is totally unique. That said, while we can promise no plagiarism from open web sources or specific databases we check, no tech out there (except Turnitin itself) can scan every source Turnitin indexes. If you want that extra peace of mind, we recommend running your paper through WriteCheck (a Turnitin service) and sharing the report with us.
Android Studio:
Android studio is the Integrated Development Environment used for developing application exclusively for Android platform.
It is a strong editor tool for developing creative User interface and emulators for different versions to test and simulate real time environment without having actual Android devices.
It also has a very useful Gradle plug-in using which you can create application files (apks) with different configurations. Moreover, it makes exporting and uploading of applications on play store easy with a single clicking. Better testing Capabilities and flexible features allows user to run main activities efficiently. It is a very useful tool to run test cases on URL connectors.
The moment you place your order, we jump into action to find the perfect writer for you. Usually, we’ve got someone lined up within an hour. Sometimes, though, it might take a few hours—or in rare cases, a few days—if we need someone super specialized. If no writers from your chosen category are free, we’ll suggest one from a lower category and refund the difference if you’d paid extra for that option. Want to keep tabs on things? You can always peek at your order’s status on your personal order page.
Hash Based Signatures
Static Malware Detection Using Hash Based Signatures
It is a method of detecting malwares using Signatures of Web Links and matching them with stored hashes. It is called static because it is matched with already stored hashes and administrator adds new hashes manually into repository in order to update it.
Virus Share
It is a repository of malware samples to provide security researchers, incident responders, forensic analysts, and the morbidly curious access to samples of live malicious code.
It consists of 337 plain text files with stored hashes per each line. Files 0-148 are 4.3 MB in size with 131,072 hashes and 149 onwards are 2.1 MB with 65,536 hashes
Cryptographic Algorithm
MESSAGE DIGEST 5(RONALD RIVEST, 1991): It is an algorithm that works as checksum to verify integrity of valid documents. The basis lies in hashing techniques. It applies hash function on files (URL, DOCUMENTS) and generate their hash as shown below
e4d909c290d0fb1ca068ffaddf22cbd0
Project Scope:
Project Deliverables
We basically focused on delivery of 3 to 4 evidences to prove the success of our project: –
1.2.3 System Organization
This section will highlight the overall working of project and dependencies of one module over another. The whole system is organized and planned to work according to implementation strategy as depicted above.
Figure 3 System Organization Steps
Figure 4 System Organization Steps 2
This chapter describes about how the implementation of malware analysis works. It specifies all the high-level techniques used and also specifies some important aspects of the project.
For our project deployment we use Android Studio software and run our website on a Nexus emulator with the help of HTML Commands. We deploy the system with an incremental approach. As we develop a program we test it, then make further changes and finally only after successful completion we move to the next step in deployment. While deploying the application the issues that should be resolved include:
Below are the installation steps of Android Studio.
The implementation approach used is the static malware detection analysis method. We use a static database from VirusShare.com which is a repository that provides a database with live malicious codes that researchers, forensic analysts and incident reporters can use. If the malware detected on our system is not in the database, we will manually add them to our database. (VirusShare). Further analysis will be done of the static analysis against strings, libraries that are linked and all functions.
The below table describes the roles, responsibilities, titles and contact details in case of any queries or any changes that are needed to be implemented on the system.
| NAME | ROLE | CONTACT NO |
| Alex Ng | Project Co-ordinator | +61 3 94793739 |
| Achhardeep Kaur | Design and Implementation | +61 4 69876192 |
| Danielle Rebello | Test case designing and documentation | +61 4 68469917 |
| Gurleen Kaur | Design and Implementation | +61 4 01879603 |
| Sonic Raithatha | Testing and documentation | +61 4 69733252 |
Here, we have got those users who are going to use the tool that we have developed. Mainly our project would have 2 major types of users.
He is a type of user who has got all the types of control in his hands. He, can make changes in the tool that is developed, add or delete things and make the tool updated with the passage of time. It is his responsibility to add hashes everytime in Virus Share and keep the database updated. So, that all the new adwares that are found are shown when a user enters the URL to check whether the site is safe or not. User will get updated results because of the administrator.
Here, it will cover all the users that are from computer background and from non-computer background. So, we have developed a tool in such a manner that whenever the results are shown to the user he will understand the result easily and do not need to study anything for understanding.
We feel because of our project they are only the 2 users who will be using our project.
In this section we talk about the major tasks or the deliverables of our project that need to be focused on during the overall implementation of our system. We mainly focus on 3-4 evidences that prove the success of our project.
A Prototype of the project involves how the front end of this project looks. The prototype view of the project is as shown in Fig. 2.1. When we input the link “http://www.wired.com” and click the “GET WEBSITE” button we will get a list of all the Adwares that are present on that website, and we can differentiate between Mal-adwares and Adwares.
An encrypted malware database in the form of MD5 hashes which was extracted from “VirusShare.com” consists of a list of 200-300 files, each having 300-400 malware samples or malicious codes. The below Fig. 2.2 provides you with a screenshot of the list of few of our MD5 hashes malware sample – VirusShare_00100.zip file.
Figure 6 Virus Share Database Example
In order to ensure that our system is running as expected we develop some test cases in comparison with the system requirements and check whether these requirements have been satisfied or not. Table 2.2 shows a list of all our test cases.
| Test Case No | Test Input | Test Scenario | Extracted Html Tag | Type | Test Result |
| 1 | URL | Check Valid URL | Img src=“https://assets.adobedtm.com” | IMG SRC | Redirecting to a different source |
| 2 | URL | Check Valid URL | Img src=“https://media.wired.com” | IMG SRC | Valid Source |
| 3 | URL | Check Valid URL | Src defer=“https://c.amazon-adsystem.com” | Script SRC | Valid Source |
| 4 | URL | Check Valid URL | Src=“https://js-sec.indexww.com” | Script SRC | Valid Source |
Table 2.3 gives details about all documentation submitted for evidence during the design and implementation of this system. ‘
| Task no | Week no | Submission date | Description |
| Task 1 | Week 3 | 13th Aug | Project Progress Report 1 – Uploaded via Turnitin |
| Task 2 | Week 5 | 27th Aug | Project Progress Report 2 – Uploaded via Turnitin |
| Task 3 | Week 6 | 3rd Sep | Project Design PowerPoint Presentation – Part A – Presentation done during lecture hours and PPT uploaded via Turnitin |
| 9th Sep | Project Design Report – Part A – Uploaded via Turnitin | ||
| Task 4 | Week 7 | 10th Sep | Project Progress Report 3 – Uploaded via Turnitin |
| Task 5 | Week 9 | 1st Oct | Project Progress Report 4 – Uploaded via Turnitin |
| Task 6 | Week 11 | 15th Oct | Project Progress Report 5 – Uploaded via Turnitin |
| Task 7 | Week 12 | 22nd Oct | Project Implementation PowerPoint Presentation – Part B – Presentation done during lecture hours and PPT uploaded via Turnitin |
| 31st Oct | Project Implementation Report – Part B – Uploaded via Turnitin |
Table 3 Document Submission Details
From week 1-6 we focused on the design of our Mal-adware Detection System. In this section, we will discuss about how the implementation (from week 7) of our system was managed based on all the tasks that were done in the allotted time period. We also focus on major tasks that were to be completed including any milestones that are dependent on the project. Table 2.4 gives a detailed description of the schedule.
| Week No | Start Date | End Date | Tasks Completed |
| Week 6 | 3rd Sep | 9th Sep | Project prototype design. |
| Week 7 due Project Progress Report 3 worked on. | |||
| Week 7 | 10th Sep | 16th Sep | Extraction of maladwares through a website link. |
| Week 8 | 17th Sep | 23rd Sep | Implementation ofMD5 hash function program. |
| Week 9 due Project Progress Report 4 worked on. | |||
| Week 9 | 1st Oct | 7th Oct | Comparing MD5 hashes – VirusShare database, with the links. |
| If it does not exist in the database, we will add them manually. | |||
| Week 10 | 8th Oct | 14th Oct | Designing test cases with appropriate inputs. |
| Comparing which are adware and which are maladware. | |||
| Week 11 Presentation PPT for rehearsal is prepared. | |||
| Week 11 due Project Progress Report 5 worked on. | |||
| Week 11 | 15th Oct | 21st Oct | Integration testing performed with each test case developed. |
| Minor improvements/changes are implemented and tested once again. | |||
| Final testing results are recorded. | |||
| Week 12 Final Presentation PPT changes are made. | |||
| Working on Final Implementation Report. | |||
| Week 12 | 22nd Oct | 28th Oct | Final Presentation and demonstration of the project. |
| Working on Final Implementation Report. |
Table 4 Implementation Schedule
Most Mal-adware detection systems tend to have security flaws that may affect the performance of the detection system. We need to secure our system from theft or damage of the hardware, software and misdirection of the service that needs to be provided. (Wikipedia). The privacy of the data that is being stored on the system needs to protect. We need to determine what data in the system needs to be protected from third parties and which data can be shared. (Rouse) .
Some of the security policy requirements that can be implemented on the system to provide better security features can be as follows,
| Item | Relevance |
| Policy on: cybersecurity; IT system security; monitoring and surveillance; integrity; access control | Security controls at the perimeter and our networks internally need to be protected against malware injection. |
| Policy on: BYOD | Specifies controls to the security on personal ICT devices used at work. |
| Policy on: Incident management and reporting | Malware incidents should be reported at the helpdesk immediately. Incidents will be resolved promptly by experts. |
| Policy on: Business Continuity | Mal-adware related events are common and serious enough to document the recovery steps, as well as contingency plan. |
| Policy on: Backups and Archives | Securely retaining offline copies of all important files that you will need to recover from malwares, ransomware attacks and other incidents. |
| Policy on: Antivirus controls | Provides details about the antivirus and other control measures. |
When we talk about the security issues we don’t feel our project will face any serious security related issues but still we will create an account with user ID and password so that the user can login and carry out the activities whenever he wants to and test for different websites and check whether the URL is secure or not.
As our team worked on Android studio for the implementation of project, So, we did not require too much of the hardware equipment. All the components that we used during implementation of this project are listed in section.
Following is the list of hardware requirements to develop our project using Android Studio:
| Hardware | Minimum Requirement | Used by Our team |
| Operating System | 64-bit distribution capable of running 32-bit applications | 64- bit Windows 10 |
| RAM | 3 GB minimum | 8GB + 1 GB for the Android Emulator |
| Hard Drive | 2 GB of available disk space minimum | 4 GB (500 MB for IDE + 1.5 GB for Android SDK and emulator system image) |
| Screen Resolution | 1280 x 800 minimum screen resolution | 1280 x 800 minimum screen resolution |
| Processor | Intel® processor with support for Intel® VT-x |
You Want The Best Grades and That’s What We Deliver
Our top essay writers are handpicked for their degree qualification, talent and freelance know-how. Each one brings deep expertise in their chosen subjects and a solid track record in academic writing.
We offer the lowest possible pricing for each research paper while still providing the best writers;no compromise on quality. Our costs are fair and reasonable to college students compared to other custom writing services.
You’ll never get a paper from us with plagiarism or that robotic AI feel. We carefully research, write, cite and check every final draft before sending it your way.