Top Essay Writers
Our top essay writers are handpicked for their degree qualification, talent and freelance know-how. Each one brings deep expertise in their chosen subjects and a solid track record in academic writing.
Simply fill out the order form with your paper’s instructions in a few easy steps. This quick process ensures you’ll be matched with an expert writer who
Can meet your papers' specific grading rubric needs. Find the best write my essay assistance for your assignments- Affordable, plagiarism-free, and on time!
Posted: July 9th, 2022
We get a lot of “Can you do MLA or APA?”—and yes, we can! Our writers ace every style—APA, MLA, Turabian, you name it. Tell us your preference, and we’ll format it flawlessly.
Context: This project puts to test the following hypothesis, “Web Services are widely deployed and play an important role in today’s Internet paradigm”. The role of web services is currently a broad aspect in research, academia and e-commerce. This is for example, numerous services such as, email, storage and cloud all falls under web-based services. Often web services comprise of a Service Level agreement (SLA), by standards defining services on offer inclusive of their characteristics. However, current SLA is more centred on Quality of Service (QoS), adversely resulting in lacking a vast content of other crucial security concerns.
Aims and Objectives: Aim to study in-depth, existing SLA standards such as WS-Agreement and WSLA, examining the possibility of extending them to incorporate other security concerns (crucial elements) such as confidentiality and integrity.
Methods: Section of the project focuseson proposal for a solution that will extent SLA security concerns, with the aim to improve the current state and bridge security gaps for other overlooked security elements such as confidentiality and integrity among others. A project proposal is derived from a combination of results obtained from internet users’ survey and existing literature on SLA security concerns.
Findings/Results: Revealed that a significant number of internet users are aware of existence of security concerns despite high dependency on the internet. Security concerns in Web-based services and SLA were also identified through literature review. The results of which is a clear indication that mitigation of security issues is a battle yet to be won regardless of the subject being widely explored in research community.
Totally! They’re a legit resource for sample papers to guide your work. Use them to learn structure, boost skills, and ace your grades—ethical and within the rules.
Conclusion and future work: Like Web Services, Service Level Agreements are faced with security challenges. This depend on the parameters on which the Service Level Agreement offers. Currently more focus has been found to be on Quality of Service. Therefore, the project is in appeal to Web Services providers and consumers to include other security concerns such as confidentiality and integrity. This is in anticipation for enhanced security in SLA through adoption of lacking parameters. Future recommendations are to review the new SLA to, identify strengths and weaknesses as well as adaptation to future requirements and contingency planning for possible dysfunctions.
Key words: Web-based service, Service Level Agreement (SLA), security concerns, Quality of Service (QoS), confidentiality, integrity
Table of Contents
Starts at $10/page for undergrad, up to $21 for pro-level. Deadlines (3 hours to 14 days) and add-ons like VIP support adjust the cost. Discounts kick in at $500+—save more with big orders!
1.1 Study Title: Analysing security in Service Level Agreement (SLA)
1.3 Concept of security concerns in SLA
100%! We encrypt everything—your details stay secret. Papers are custom, original, and yours alone, so no one will ever know you used us.
1.4 Problem and hypothesis analysis
Nope—all human, all the time. Our writers are pros with real degrees, crafting unique papers with expertise AI can’t replicate, checked for originality.
1.8 Relevance and Significance
1.9 Overview of the project structure
2.1 Definition of Web Services
Our writers are degree-holding pros who tackle any topic with skill. We ensure quality with top tools and offer revisions—perfect papers, even under pressure.
2.1.2 Web Services architecture
Figure 1. Web services architecture
Web Services Architecture roles
How a Web Service Architecture Operates
Experts with degrees—many rocking Master’s or higher—who’ve crushed our rigorous tests in their fields and academic writing. They’re student-savvy pros, ready to nail your essay with precision, blending teamwork with you to match your vision perfectly. Whether it’s a tricky topic or a tight deadline, they’ve got the skills to make it shine.
2.2 Understanding Service Level Agreements (Answers to Research Questions)
2.3 Linking SLA to Web Services and addressing security issues
Figure 2. Interoperability in web services
Guaranteed—100%! We write every piece from scratch—no AI, no copying—just fresh, well-researched work with proper citations, crafted by real experts. You can grab a plagiarism report to see it’s 95%+ original, giving you total peace of mind it’s one-of-a-kind and ready to impress.
2.4 Existing Service Level Agreements
Table 1. Questionnaire results
Table 2. Question 1 data analysis
Yep—APA, Chicago, Harvard, MLA, Turabian, you name it! Our writers customize every detail to fit your assignment’s needs, ensuring it meets academic standards down to the last footnote or bibliography entry. They’re pros at making your paper look sharp and compliant, no matter the style guide.
Table 3. Question 2 data analysis
Table 4. Question 3 data analysis
For sure—you’re not locked in! Chat with your writer anytime through our handy system to update instructions, tweak the focus, or toss in new specifics, and they’ll adjust on the fly, even if they’re mid-draft. It’s all about keeping your paper exactly how you want it, hassle-free.
Table 5. Question 4 data analysis
Table 6. Question 5 data analysis
It’s a breeze—submit your order online with a few clicks, then track progress with drafts as your writer brings it to life. Once it’s ready, download it from your account, review it, and release payment only when you’re totally satisfied—easy, affordable help whenever you need it. Plus, you can reach out to support 24/7 if you’ve got questions along the way!
Table 7. Question 6 data analysis
Table 8. Question 7 data analysis
Need it fast? We can whip up a top-quality paper in 24 hours—fully researched and polished, no corners cut. Just pick your deadline when you order, and we’ll hustle to make it happen, even for those nail-biting, last-minute turnarounds you didn’t see coming.
Table 9. Question 8 data analysis
Table 10. Question 9 data analysis
Absolutely—bring it on! Our writers, many with advanced degrees like Master’s or PhDs, thrive on challenges and dive deep into any subject, from obscure history to cutting-edge science. They’ll craft a standout paper with thorough research and clear writing, tailored to wow your professor.
Table11. Question 10 data analysis
Table 12. Question 11 data analysis
Table 13. Question 12 data analysis
We follow your rubric to a T—structure, evidence, tone. Editors refine it, ensuring it’s polished and ready to impress your prof.
Table 14. Question 13 data analysis
Send us your draft and goals—our editors enhance clarity, fix errors, and keep your style. You’ll get a pro-level paper fast.
3.4.1 Requirements definitions for SLA
SLA Measurable requirements (Qualities)
SLA unmeasurable requirements (Qualities)
3.5.1 Proposed solution: An Approach to Secure Service Level Agreements
Yep! We’ll suggest ideas tailored to your field—engaging and manageable. Pick one, and we’ll build it into a killer paper.
CHAPTER 4: CRITICAL ANALYSIS OF PROPOSED SOLUTION
4.1.3 Proposed solution limitations
CHAPTER 5: EVALUATION, CONCLUSION AND FUTURE WORK
Yes! Need a quick fix? Our editors can polish your paper in hours—perfect for tight deadlines and top grades.
Appendix 1: Analyzing security in Service Level Agreement questionnaire based Survey
Appendix 2: Survey respondent Consent
Appendix 3: Records of monthly supervision meetings
Sure! We’ll sketch an outline for your approval first, ensuring the paper’s direction is spot-on before we write.
Appendix 4: Report Structure Documentation
Definitely! Our writers can include data analysis or visuals—charts, graphs—making your paper sharp and evidence-rich.
We’ve got it—each section delivered on time, cohesive and high-quality. We’ll manage the whole journey for you.
Yes! UK, US, or Aussie standards—we’ll tailor your paper to fit your school’s norms perfectly.
Chapter overview
If your assignment needs a writer with some niche know-how, we call it complex. For these, we tap into our pool of narrow-field specialists, who charge a bit more than our standard writers. That means we might add up to 20% to your original order price. Subjects like finance, architecture, engineering, IT, chemistry, physics, and a few others fall into this bucket—you’ll see a little note about it under the discipline field when you’re filling out the form. If you pick “Other” as your discipline, our support team will take a look too. If they think it’s tricky, that same 20% bump might apply. We’ll keep you in the loop either way!
This chapter introduces the project giving an insight to its hypothesis, “Web Services are widely deployed and play an important role in today’s Internet paradigm”. Security concerns are at the core of the discussions in the study. Focus is more directed to lack of security concerns in Service Level agreement (SLA) such as, confidentiality and integrity, and their role in SLA. The role of web services in today’s internet paradigm and SLA security concerns are to be explored in elaboration to the hypothesis. Study title, motivation and background, concept of security in SLA an insight to the problem and hypothesis analysis, research aims and objectives, research questions, relevance and significance will be included. Finally, in conclusion to the chapter is an overview of the project structure.
Security concerns are remaining a huge focus on today’s internet paradigm (Aljazzaf et al, 2010; Toms, 2004; Wang and Vassileva, 2007; Zhou et al 2014). This is for example in widely deployed/distributed computing services of huge importance to the current internet paradigm. For instance, cloud computing, email, storage, all falling under web-based services (Toms 2004). “Web Services” can be defined as systems using Extensible Mark-up Language (XML) in communicating among distributed computing environments (Park et al 2007; Zhou et al, 2013). Latest businesses are now functioning globally through exploitation of web services by distribution of their applications (Frankova 2010). Web services researchers have a more focus on security research on establishing safety regulations for services (JIANG et al 2016; Park et al 2007). Often exploitation of web services comes with a regulatory agreement between themselves and consumers on what services they offer and any consequences because of breach (Meland et al 2012). An example of web services security regulations is a Service Level Agreement (SLA). SLAs has a relationship regulatory role between the providers and consumers (Meland et al 2012). This project is going to focus on analysing Service Level Agreement security concerns beyond Quality of Service (QoS), which is currently the focus of SLA, lacking other crucial security concerns such as confidentiality and integrity (Zhou et al 2014). In addition to the analysis of SLA, a proposal will be made to extend security concerns in SLA to include confidentiality and integrity as crucial aspects in security. Three objectives are to be satisfied as follows;
Our writers come from all corners of the globe, and we’re picky about who we bring on board. They’ve passed tough tests in English and their subject areas, and we’ve checked their IDs to confirm they’ve got a master’s or PhD. Plus, we run training sessions on formatting and academic writing to keep their skills sharp. You’ll get to chat with your writer through a handy messenger on your personal order page. We’ll shoot you an email when new messages pop up, but it’s a good idea to swing by your page now and then so you don’t miss anything important from them.
Web-based services are among widely distributed and dominant technology on the internet, with many diversified services (JIANG et al 2016; Masood and Java 2015; Toms 2004). Such is a dilemma for consumers in terms of making a choice as all equally functional, possibly differing in cost, quality and security (Zhou et al 2014). They are featured with “self-contained and self-descriptive” applications composed of modules that are invokable on the internet once deployed. Currently, web-based services are the most favourable medium for exchanging information (Toms 2004). These modular applications (self-contained units) are platform independent (Tidwell 2000; Zhou et al 2014). Web services operate on a Service Oriented Architecture (SOA) (Park et al 2007; Zhou et al, 2013). For instance, research by Zhou et al, 2014, identified majority studies to have a significant concentration on Quality of Service aspects not fully addressing security concerns. Cloud computing is also vastly growing providing Infrastructure, Software or platform as a service. All either exposing or consuming Web Services from another platform or Infrastructure. Consequently, results in complex interaction management, adversely making it difficult to manage the security aspect of things (Baun et al. 2011; Deshmukh et al 2013). A significant number of contributions from research community indicates proven factors that the security challenges battle in distributed computing is continuous (CSGE, 2014; Kumar et al 2015; Mukherjee et al 2013; Schwarz et al 2005). This makes it a more crucial requirement for the service providers to tighten up security measures while giving the consumer some form of guarantee that they are to satisfy certain security parameters apart from the traditionally known focus on Quality of Service (QoS) (Zhou et al 2014). Example of a guarantee of services from the provider of web-based services is a Service Level Agreement (Undheim, Chilwan, & Heegaard, 2011, p. 2). This project is motivated by exploring and investigating SLA security concerns beyond Quality of Service (QoS). Findings drawn from the in-depth study forms the basis for deciding whether it is feasible to propose a solution to improve security concerns in SLA.
Casola et al (2015) addressed questions as to whether security can be provided in form of a service, or could a SLA be sufficing in meeting security requirements. These questions are no doubt a centre of controversy in web-based services. In support to that fact, Bianco et al 2008; Zhou et al 2014 pointed that despite security challenges faced in the SOA, majority of current SLA focus is more directed in Quality of Service. This is evident that it is a shared view that current SLAs are rather based on quality provision, not making it clear to consumers of underlying security concerns compromising the so called “Quality of Service”. Given such, security issues that may rise because of failing to implement a Service Level Agreement with more coverage of security concerns may be overwhelming. Security measures in a diversified environment may be quite challenging due to data complexity (CSGE, 2014; JIANG et al 2016; Kumar et al 2015; Mukherjee et al 2013; Schwarz et al 2005). Therefore, it should be in the best interest of web series providers to give maximum security assurance to their consumers in SLA. Such is paramount in establishing strong business relationships in web services (Belanger et al 2002). Numerous research indicates that the appalling rate of security issues in e-commerce makes it hard to win the trust of consumers (Belanger 2002; Cyra and Górski 2008; Motallebi et al 2012; Aris et al 2011). This opens argumentative ideologies such as whether a more secure SLA may prove a positive difference? It is anticipated that some of the questions are to be answered in this study. Inclusion of security concerns such as confidentiality and integrity to QoS is the basis on which this study aims at answering some of such questions.
This project puts the following hypothesis to test, “Web Services are widely deployed and play an important role in today’s Internet paradigm”. What makes web services unique is that despite being made by different companies they are interoperable. Their interoperability enables them to discover and communicate among themselves (Li-jie Jin et al 2002). The wide deployment means a large pool of services with same functionalities are located and invoked (Zhou et al 2014). Zhou et al (2014) views systems with huge diverse resources as the most vulnerable to security challenges while, JIANG et al (2016) echoes the same idea. As web services deployment vastly expands to accommodate the increasing demand of the new trend, so does the security concerns (CSGE 2014; Mukherjee et al 2013). To establish more security and consumer satisfaction in web services, security concerns must be prioritised (Zhou et al 2014). It is in the interest of service providers attend to numerous security concerns that may affect consumers and cost them money. This is crucial in delivering secure services to consumers as a competitive weapon in business (Belanger et al 2002). There have been many efforts done to regulate services as a measure to promise users security (Kelly 2012; Tomlinson and Lewicki 2015; Undheim, Chilwan, & Heegaard, 2011, p. 2; Verma 2004). Increased deployment of web services to cope with consumer demands, results in interaction complexity between providers and consumers. Therefore, security hold the key to protection of interactions (Deshmukh et al 2013).
Overall, this study is aimed at analysing existing SLA security concerns in web – based services to identify lacking security concerns.
Focus is directed in achievement of the aim through investigating security concerns in Service Level Agreement of web-based services. This is to establish the basis of which a solution can be proposed to extent SLA security concerns through inclusion of confidentiality and integrity in current parameters.
To explore and suffice the requirements of the hypothesis being put to test, existing literature is to be studied to investigate the following;
Based on the research aims in 1.5 and research objectives in 1.6, the following research questions have been formulated;
RQ1. What is the role of SLA in Web Services?
Formulation of this research question is based on identifying the importance of SLA in web services. Answers to RQ1 will give an understanding of security issues affecting web services and relevancy of SLA.
RQ1.1 What are relevant security threats affecting SLA?
RQ2. What SLA security parameters currently exist in Web services?
The key objective to this question is based on investigating current focus on security in SLA to identify lacking security parameters. This will assist in suggesting what can be done to include new parameters that can provide enhanced security in SLA.
RQ3. Who has the responsibility to ensure security concerns are investigated in SLA?
This question assists in identifying who is accountable for initiating and deploying SLA.
RQ4. Do Web services achieve an added value from SLA?
This question analyses effects of adding new security concerns to the consumers. Formulation of the question is useful as the web services providers interest lies on establishing and building strong relations with consumers. Therefore, it crucial to establish security as a token for enhanced SLA.
In consideration to web-based services such as cloud computing, email, storage, it is crucial to establish Service Level Agreements fit for purpose. This is crucial as part of contractual agreements as it establishes trust into the service provider by the consumer (Dukee 2010; Li-jie Jin et al 2002; Verma, 2004). A Service Level Agreement (SLA) is a consensus/agreement as part of a contract between two parties namely, service provider and the service consumer (user), (Kelly 2012; Tomlinson and Lewicki 2015; Undheim, Chilwan, & Heegaard, 2011, p. 2; Verma 2004). The SLA is made up of parameters offered to the consumer by the provider. The SLA underlines the expectation of the customer from the service providers, as well as addressing the obligations of both the parties partaking in the agreement. The service provider is under obligation to provide services being paid for by the consumer. Failure to which the service provider consequently suffers financial reparation’s (Li-jie Jin et al 2002). Additionally, and most importantly, SLA includes the terms regarding availability, performance and security of the service among other parameters from the provider’s end, inclusive of all that is to be adhered once the agreement takes place (Verma, 2004). From the provider’s side, this guarantees service provisions while the consumer signs in agreement to what is offered to them. The agreement between the two stakeholders is voluntary. However, the term “agreement” is not as easy as the word sounds, for both stakeholders to reach to that stage, it may take a lot of controversial ideologies about parameter expectations (Kelly 2012; Tomlinson and Lewicki 2015). A yet another difficult situation, “negotiation” will be faced in compromise to reach an agreement by both parties’ through surrendering a certain measure of their freedom. Negotiation becomes necessary where there are conflicting ideas (Tomlinson and Lewicki 2015). A comprehensive study is to be taken in anticipation to assist both stake holders understand each other’s view point to ease the agreement process (Hamilton 2015). To overcome security holes resulted on failing to implement security measures that will protect the current SLA from security vulnerabilities, this study proposes a solution. Therefore, relevancy and significance is formed efforts to seal security holes in SLAs, by proposing a more secure SLA.
Considering the overwhelming size of the project, this section act as a project pointer as it gives an overview of how work is being approached as follows;
Chapter 1: This is formed of an introduction to the project, hypothesis (main subject of the study), “Web Services are widely deployed and play an important role in today’s Internet paradigm”. Title of study, Motivation and background, security concerns in Service Level Agreement (SLA), problem and hypothesis analysis, aims and objectives are all in the first chapter. Research question are to be addressed with justification for significance of study and rationale.
Chapter 2: Second chapterexplores Service Level Agreements and related security concerns, including existing literature review. More focus on this chapter is centred on literature review for establishment of security concerns. To give an understanding of the subject, an overview of web services, and that of SLA. Overviews are to establish the relationship between web services and SLAs in detail. The outcome of studying existing SLAs will determine proposition of a solution that will extent SLA security concerns, with the aim to improve the current state and bridge security gaps for other overlooked security elements.
Chapter 3: Design and development work is undertaken in this chapter. This is where requirements specifications for proposing a solution that will extend security concerns in SLA will be addressed. A combination of results from questionnaire survey and literature review form the basis of proposing a solution. This is an action executed to reduce security holes resulted due to more focus on (QoS) in current SLAs.
Chapter 4: Critical Analysis of Proposed Methodology or Artefact will take place in this chapter. An overall analysis will be made to outline the origin of the proposal ideology, the proposed solution, advantages and disadvantages that are likely to result. Also, limitations of the project.
Chapter 5: Evaluation of the proposed solution will take place on this chapter discussing methods for evaluation including results from the discussion. Overall work done throughout the project will be discussed in summary to all previous chapters. Most importantly project conclusion and the direction of project future.
Chapter overview
An in-depth study of existing work on existing SLA standards such as WS-Agreement and WSLA, investigating their content to identify the extend in covering security concerns, such as confidentiality and integrity. Results of the investigation anticipate identifying security holes or shortfalls such as lack of focus on confidentiality and integrity. To give a clear picture of the study elements, the chapter will start with an overview of web services and Service Level Agreements. More focus of the overview will be on security concerns as they are the basis of the work undertaken in the project. Results from the literature review will contribute to the establishment of an idea to be used in proposing a solution for incorporation of security concerns such as integrity and confidentiality.
2.1 Definition of Web Services
Web services are among the growing software architecture trends. They do not have a standard definitive term but various terms (Xiang, 2007). Software components build to operate platform-independently, are defined as web services (Li-jie Jin et al 2002; Zhou et al 2014). Web services have provided dynamic interoperability among in e-commerce (Wang et al, 2004). Once deployed, they are discoverable and invokable by other applications (Fensel and Bussler, 2002). Cloud is an example of Web -based services currently being viewed as the IT industry backbone (El-Awadi et al., 2015; Toms 2004). Figure 2.1.2. elaborates the typical architecture of a web services. However, the architecture is not limited to the attributes in 2.1.2. Composition varies with considering of principles and parameters included. Justification of diagram choice for illustration of web services architecture in this study is based on relevancy.
2.1.2 Web Services architecture
Figure 1. Web services architecture
(Balaji et al, 2013).
Web Services Architecture roles
How a Web Service Architecture Operates
There are three contributory elements through which web services can be exploited as follows;
publish, find and bind (Kreger, 2001).
A publication describing the service, a quest for the service, followed by invocation of a service(s).
2.2 Understanding Service Level Agreements (Answers to Research Questions)
Consumers have lately been faced with being indecisive on which services among the widely distributed and diversified web services due to competitive providers. As an intervention strategy to the situation, a mechanism to overcome that becomes necessary in form of a contract. This contract is used to initiate negotiations and is known as a Service Level agreement (SLA). SLA has a centralized role through assisting service providers in the process of defining services to be delivered to consumers (Bouras et al., 2005). Answering research questions below will define the role of SLA in web services, address security threats affecting SLA, outline existing SLA security parameters in web services, clarifying stake holder responsibilities and suggest the value of SLA to web services.
RQ1. What is the role of SLA in Web Services?
A service level agreement (SLA) refers to a contract between the service provider and its internal as well as external customers that details what services will be rendered by the provider and the level or standards of performance that will be met by the provider. A major of the SLA is establishing customer expectations in respect to the standard of performance and the quality of work to be rendered by the provider (Kelly 2012; Tomlinson and Lewicki 2015). SLA helps the parties define the availability and uptime of the services, that is, it helps set the percentage of time the services will be available. SLA key performance benchmarks are developed upon which the actual performance will be compared. This ensures quality work throughout the stipulated time. SLA also provides a notification schedule respect to failure or network issues. In addition, it will indicate the expected response time for the different type of issues that may arise. SLA provides a documentation of how a downtime will be addressed and how the customer will be compensated in case of a contract breach. Security promises are also outlined in SLA, although presently, most research materials seem to have a concentrated focus in the Quality of Service Aspects. Research by Bouguettaya, 2013 regards SLA as posessing or serviong as a composion of blueprint and guarantee for cloud services.
RQ1.1 What are relevant security threats affecting SLA?
There are numerous security threats affecting SLA as identified by the European Network and Information Security Agency (ENISA) (2009) make sure this is appearing in master ref list. SLAs are more than often affected by loss of governance. This happens especially at the drafting of the SLAs where most of them are poorly drafted and affected by customer not being specific during the drafting process (reference if possible). Research suggests that when SLAs are not soundly deployed will have adversities (Li-jie Jin et al 2002; IBP, 2013).
RQ2. What SLA security parameters currently exist in Web services?
Casola et al, (2015) expresses security as existing among factors representing major limitations in adopting cloud computing. They mentioned this is due to lack of transparency in how service providers grant security, but rather focusing on service aspects such as availability and performance. Where secure SLAs are implemented and deployed, proves security can be offered as a service. Zhou et al, (2014) echoes that security should be treated as a priority for achievement of established consumer satisfaction in web services. They also pointed that current SLA is overshadowed by Quality of Service. This is evident that security parameters are yet to be dominant in web services SLAs.
RQ3. Who has the responsibility to ensure security concerns are investigated in Service Level Agreements (SLA)?
Service level agreements are based on agreement between the provider, consumer and any third party (Kelly 2012; Tomlinson and Lewicki 2015). However, for that agreement to be reached, it somehow originates from the provider as it describes services which the provider is willing to commit to provide (Bouras et al., 2005). In this case, the provider initiates the SLA to guarantee services to the consumer. From consumers’ perspective, it is the description of expectations such as quality of services (Bianco et al 2008). To reach to a consensus, an SLA is drafted outlining provider and consumers’ obligations and responsibilities (Bouras et al., 2005). During the entire lifecycle of the SLA, more responsibilities require service providers to ensure they meet their security promises through investigation any security issues. (Li-jie Jin et al, (2002) mentioned that should the service provider fail to meet their obligations, this may have adverse effects such as financial loss. In consideration to findings, the answer to this question identifies the service provider as the party accountable for initiating and deploying, and reviewing SLA.
RQ4. Do Web services achieve an added value from SLA?
Using Service Level Agreements (SLAs) in web services is essential for provision of added value (Soomro, Aijaz, Ahmed 2016). This ensures consumer satisfaction due to successful deliverance of Quality of Service (QoS) as expected. Availability, reliability, performance and quality of services are all defined by the SLA. SLA definition also includes ensuring timely, safe and secure message or information delivery (Bianco eta l, 2008). A well implemented SLA satisfying crucial security elements such as confidentiality and integrity offers added value to web services (CISCO, 2005; Soomro, Aijaz, Ahmed 2016). By satisfying security requirements in SLA deployment, trust is built in consumers, thereby resulting in the web services being able to cease more business opportunities with consumers through recommendations (Zeginis and Plexousakis, 2010). Unlike placing entire responsibility on the service provider, SLAs establishment follows a two-way service accountability. This means consumers are also responsible for failure to abide by agreed SLA terms and conditions (CISCO, 2005). In the service lifecycle, SLAs play a critical role through influencing engineering and operational decisions. Popularity of cloud computing is partly due to SLA implementation (Müller et al. 2014). SLAs are used widely in service-oriented architectures and distributed systems. Through these agreements, entities can agree on what services will be offered and with clearly agreed terms for delivery. Service level agreements also include who will be responsible for completion, execution, privacy aspects, and potential failures. More importantly, SLAs are limited to the description of responsibilities and expectations. The best way to understand these agreements is to break them down into schemas, negotiation protocols, SLM management, and implementations (You et al. 2015). A service level agreement cannot guarantee the availability of the service described. Additionally, it cannot deliver a good service out of a poor one. However, it can mitigate the risk of subscribing to a bad service (You et al. 2015). An SLA suitable for purpose enforces service provision and limits (Casola et al, 2015). A service level agreement needs supporting tools and mechanisms applied during different phases of its lifecycle, which requires monitoring of service execution adherence to the shared terms and enforcement. The figure below shows the SLA lifecycle;
(IBM Version 8.5) requires relocating ref and add to list. If not to replace diagram
2.3 Linking SLA to Web Services and addressing security issues
There is a wide coverage research on SLAs (Clark and Gilmore 2006; Miller 2012; Stanik et al 2014). However, it is a proven factor that majority existing SLAs are lacking confidentiality and integrity while focusing more on Quality of Service (Zhou et al 2014). The scenario in figure 2 below, shows how web services are exploited and gives an analysis of elements that consumers are likely to be enticed by, to an extent of prioritising Quality of Service. This indicates the focus on Quality of Services seem to have a stronghold in relationships between providers and consumers (Mani and Nagarajan 2002). Current research suggests that Service Level agreements on a Service Oriented architecture focus on Quality of Service (QoS) (Bianco et al 2008; Zhou et al 2014). Dukee (2010) suggested SLAs are a form of security to the consumer as compensation is provided in breach of the agreement. El-Awadi et al (2015) pointed out there is a lot of scepticism from numerous consumers relating cloud providers’. The scepticism is a result of the gap between their Quality of Service promises and what the SLA has on offer. As a result, focus on QoS with diverted attention from other security parameters, potentially resulting in economic adversities has been identified in this study as an unresolved issue that has existed for a long time (Li-jie Jin et al 2002).
The pictorial diagram below, named figure 2 is a typical demonstration of web services interoperability in day to day business between the providers and consumers (Li-jie Jin et al 2002). In the picture, Ouzzanni and Bouguettaya (2004), gave a three-step scenario a consumer named Ravi takes in planning his journey. In step (a) Ravi makes a query for an air ticket with 3 air lines named Western Air Lines, Alpha Airlines and Unified Airlines. In step (b) Ravi makes a query for accommodations among Country Hotel, StayInn and Blueridge Inn, then (c) a car from a rental company between SmartCars, CarForLess, MegaHertz. All the required services for Ravi’s quest are accessible in a large pool (Frankova 2010). An in-depth analysis of the diagram above proves the fact that the consumer’s quest is more focused on elements such as “best quality” which is to do with transactional Quality of Service (QoS) in Web services (Bianco et al 2008). Based on QoS focus of web services, my assumption is that SLA focus in pursuit of the same idea may be to satisfy consumers passion for quality. The final decision made by Ravi indicates that Quality of services is at the top of consumers’ priorities followed by others such as cost and availability among others. It is therefore necessary for providers to put more effort in addressing security parameters such as confidentiality and integrity. This study anticipates that Extending security concerns to SLA to include confidentiality and integrity, may positively add value to SLA.
Figure 2. Interoperability in web services
(Ouzzani and Bouguettaya 2004)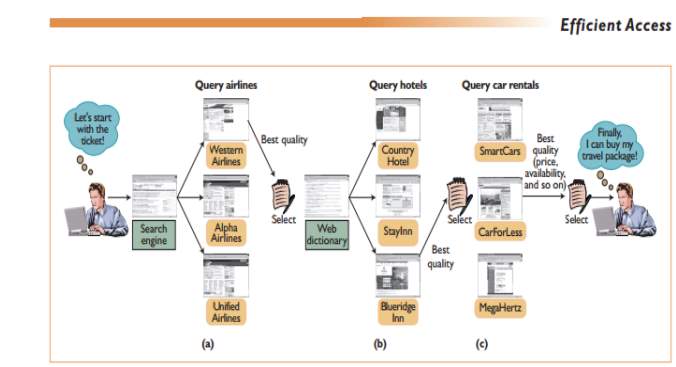
2.4 Existing Service Level Agreements
Investigating the extend in which security concerns such as confidentiality and integrity are covered in existing WS-Agreement and WSLA,
Chapter overview
Work in this chapter focuses on proposing a solution to extend security concerns to incorporate confidentiality and integrity. Questionnaire based survey results are to be included in this section and identified security holes from literature review will be addressed, followed by a suggested solution to improve security in SLA. A suggested solution will be used for as project proposal for improvement.
3.1 Questionnaire Survey
A questionnaire is a research tool used in obtaining information from a representative population selected to take part in a survey. Information obtained through questionnaires is motivated by various reasons such as identifying consumer trends, patterns, opinions and trends. Questionnaires with the objective to analyse results are normally made up of closed questions. The objective of this survey is to collect information relevant to web services consumers and their online behaviour, while abiding to Data Protection Act 1998 (Tipping, 2016). Data protection Act is in force in the interest to protect information relating to individuals. This makes it illegal for the individual conducting a survey to use data in any way apart from what it had been obtained for (Tipping, 2016). Displaying that data in one table makes it easier to count number of opted answers for each question. By so doing it makes it easier to plot charts/graphs for analysing the results. This also eases the process of converting data to information for presentation to individuals whom it may need to be shown to (Durbin, 2004) A questionnaire based survey has been used in this project for consumer involvement. Results drawn from the survey ascertains relevance of the survey to the study. An in-depth results analysis has been done on each question in this study. This has been done with consideration to make it easier for disseminating information as there are many questions.
3.1.1 Survey Data Results
Key:
P1 to P20 = Participant 1 to participant 20
Q1 to Q13 = Survey Questions
Numbers for example 5,3,1,2 represent opted answers in the survey by each participant. The table had been designed in way that makes participant numbers to tally with their opted responses and question numbers.
Table 1 is made up of all the data results from the questionnaire survey. P 1 to P 20 represents number of participants to promote anonymity in the survey.
Instructions for using table 1 data
Formation of table 1 has been formulated as a time management strategy. This has been done by displaying all data from the survey in one table for use in analysing results.by so doing it makes it presentable rather than having to keep counting responses throughout the analysis. The following is a breakdown on how table 1 has been used in displaying all results;
Using a combination of P1 to P 20 and Q1 to Q13, numbers in between are opted responses to be matched with participant, question number. By so doing, small tables of data had been produced faster for all questions. 3 D pie charts displaying results in fractions (%) had been produced using data from results obtained from each question. For more clarification, reference can also be made through the key above.
Table 1. Questionnaire results
|
|
Project Questionnaire responses | |||||||||||||
You Want The Best Grades and That’s What We Deliver
Our top essay writers are handpicked for their degree qualification, talent and freelance know-how. Each one brings deep expertise in their chosen subjects and a solid track record in academic writing.
We offer the lowest possible pricing for each research paper while still providing the best writers;no compromise on quality. Our costs are fair and reasonable to college students compared to other custom writing services.
You’ll never get a paper from us with plagiarism or that robotic AI feel. We carefully research, write, cite and check every final draft before sending it your way.